– Table of Contents
| 1. Diagnose Hacked WordPress Site |
2. Be Prepared for future |
| 3. Shut down your site temporarily |
4. Regenerate WordPress salts and security keys |
| 5. Change all WordPress passwords |
6. Take Full backup of WordPress theme and other important files |
| 7. Take WordPress Database Backup |
8. Use GWT and Google Chrome to identify malware issues. |
| 9. Search WP files for malicious code |
10. Scan WP folders for malicious files |
| 11. Find Hidden IFRAMES |
12. Check User generated Content (UGC) |
| 13. Check location of open redirects |
14. Scan internal and external links of your website |
| 15. Check Final destination Of Website traffic |
16. Scan Downloadable WP files |
| 17. Check your wp-config.php file |
18. Scan your .htaccess file |
| 19. Scan Vulnerable WP plug-ins |
20. Find and delete backdoors |
| 21. Look for hidden administrators |
22. Scan your computer for Trojans & Viruses |
| 23. Change your web hosting service provider |
24. Visit and use “Code Guard. |
| 25. An ultimate solution – intrusion tests |
|
We all use WordPress on a daily basis as bloggers, regardless of our experience or expertise.
WordPress security is a topic of vital importance for all website owners. Google blacklists thousands of hacked WordPress sites every week that are infected with malware. To be conscientious, you must follow good WordPress security and maintenance practices.
When your WordPress website is hacked, you must use WordPress Malware Removal plugins, remove malicious code from the WordPress website, or clean WordPress infection.
Wordfence plugins is used in WordPress sites for WordPress Malware Removal. The best malware scanner or plugin for redirect or WordPress malware removal.
Here are the best tips to help you find and WordPress Malware Removal database or clean malware from wordpress sites in this 2022-23 edition of WordPress Malware Removal Checklist for WordPress.
“Just, in case you have missed, have a look at our WordPress Maintenance Checklist & WordPress Security Guide too”
The security of your WordPress website is not just about clean WordPress infection but also about preventing risks. Here is the complete checklist:
When a website is hacked and WordPress finds malware, files are usually deleted, elements change, and some services stop working.
You might find it interesting to analyze the server and the site looking for traces of a hacker, whether just to get a feel for it or just to check.
We also follow these steps at WP Hacked Help when identifying malware on WordPress sites.
- Observe external messages from Google
Google typically displays the phrase “This site may damage your computer” or “This site may be hacked” in its search results.
You may need to use your antivirus or another tool such as Google Safebrowsing to detect the site as malicious
http://www.google.com/safebrowsing/diagnostic?site=mysite.com
(Note: Replace “mysite.com” by your site).
If you use Google’s Webmaster Tools, you’ll have a warning about the Google blacklist
Here’s more information from Google: http://www.google.com/webmasters/hacked/
Your browser can also warn you:
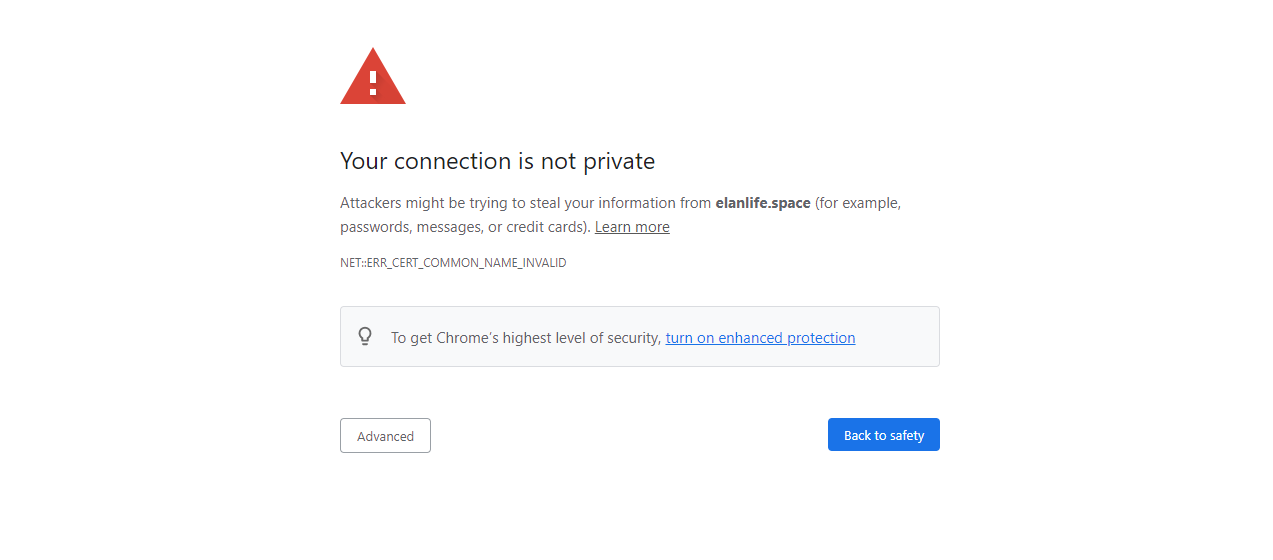 The following example comes from the Chrome browser.
The following example comes from the Chrome browser.
You may also notice something suspicious in your own logs (activity records) and believe an intrusion is likely. For this, we can look for suspicious error messages in the logs (activity records) of the web server. For this, URL Void or Virustotal can be used as well as log WordPress scanners.
There are also classic commands to retrieve the contents of the logs directory (/var /log).
It’s easy to spot an unusual IP address because it does not match your IP address.
Finally, you can also see the last modified files in the last 24 hours (1 * 24) using the following Linux command :
find / directory-to-observe -mtime 1 -print | more
Make sure you follow good practices after you recover so it doesn’t recur.
The following are some good practices:
Backing up your files regularly will make it much easier for you to recover from an attack. Don’t forget to back up your database, your important files, and everything you need.
- Cookie cutter list provided by web host
A “cookie cutter” list will not help you
As they say, experience makes the best teacher, especially when you’re dealing with something as awful as malware attacks.
- A list of control clubs is sent to you by your host so you can repair the malware on your own.
- Google sends you a list of cookies to repair the malware yourself after you contact them.
- Sometimes, you follow these instructions and remove malware from your computer.
Most of the time, these lists don’t work.
Why cookie cutter list wont help you?:
- First, to follow the instructions given in this list, you must understand your CMS (Content Management System).
It is important to know what you are doing and how it will affect website performance.
You could end up deleting the entire database or the files from your website if you make the wrong decision.
- Second, you need to know exactly where to look and what to do to fix the malware problem.
Despite recent malware attacks on Russian websites, I was quite convinced that such services could no longer be relied upon.
The services claim to protect your website from malware, which in my opinion constitutes a marketing scam.
While they scan your website for malware, they do nothing to prevent it from becoming infected.
Almost all of them scan your website once a day, and one day is enough for a hacker to inject malicious software.
You will also receive a malware warning from Google within one day if your website is infected with malware.
My experience shows that none of these services can alert you to malware problems faster than Google.
My experience with these so-called malware protection companies has been terrible. They have all failed miserably to find and alert me to malware problems in a timely manner.
There is no doubt that Google Chrome is one of the best malware scanners out there.
There is no paid malware scanner that detects malware faster than Google Chrome.
In order to ensure the security of our website, I have done a lot of work and research.
As a result of this pursuit, we created a WordPress malware scanner that you can download.
If you detect malware on your website, you should immediately remove it to prevent hackers from exploiting it.
Beware, at times a site can get stuck in maintenance mode. In that case, please read our article on How to Fix WordPress Stuck in Maintenance Mode.
For SEO-friendly maintenance of your site, follow these steps:
The first step is to create a “Maintenance mode” on the Web page. Name it 503.php.
Add the following PHP code to the top of the page (before the html> tag):
<?php
header(“HTTP/1.1 503 Service Temporarily Unavailable”);
header(“Status: 503 Service Temporarily Unavailable”);
header(“Retry-After: 3600”);
?>
A 503 response header indicates to the search engine that your website is temporarily unavailable.
In the “Retry-After” setting, search engines will try to crawl the website after 3600 seconds (or one hour).
NOTE: If your website is under maintenance, Google recommends returning status code 503.
To track visitors to the website during idle time, insert the Google Analytics tracking code on page 503.php.
Step 2: At the top of your .htaccess file, add the following code:
RewriteEngine on
RewriteCond %{REMOTE_ADDR} !^111\.111\.111\.111
RewriteCond %{REQUEST_URI} !/503.php$ [NC]
RewriteRule .* /503.php [R=302,L]
All pages on your website will be redirected to page 503.php by the code in the .htaccess file.
In this way, no matter which page a visitor accesses on your website, he or she will be automatically redirected to page 503.php. You can learn How to Fix WordPress Stuck in Maintenance Mode.
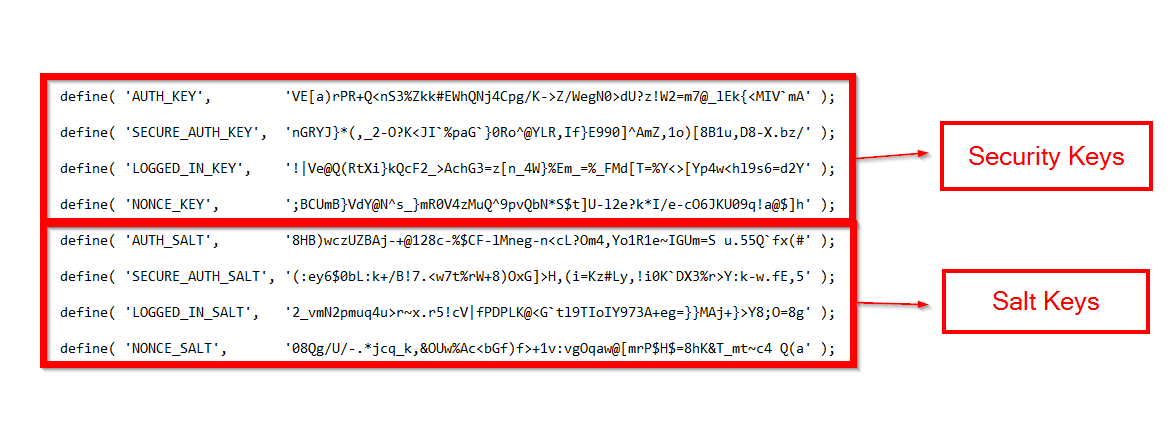
You can make your website more difficult to hack by using four different security keys that WordPress uses to encrypt information stored in users’ cookies.
Secret keys are randomly generated character strings that are used with four different salt types.
If you open your wp-config.php file, you can see the security keys and salts:
To make your website more difficult to hack again, you must change all your security keys and salts.
The only caveat is that all users who can connect to your site will have to reconnect.
As with your usual passwords, you do not have to remember or store these keys.
Don’t share them either.
Manually changing the value of these keys (using a long, complex string generated at random, as shown in the image above) or using the official WordPress salt key generator is also an option.
Changing the passwords for your WordPress admin panel, hosting control panel, FTP account, and specifically your database will help prevent hackers from gaining access to your website.
The Database section of your hosting control panel allows you to change the password for your database.
If you change the password for your database, you must immediately update the password in your wp-config.php file.
You will receive the error message “Error establishing a database connection” if you do not do this.
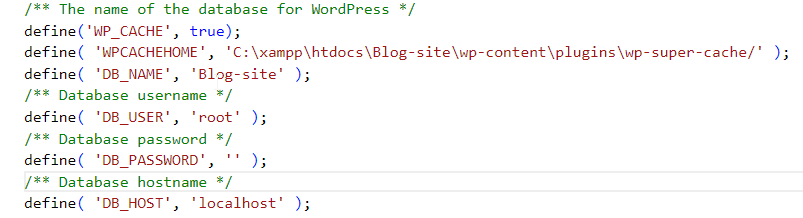
Navigate to your ‘wp-config.php’ file via the ‘File Manager’ and locate the following section:
/* The name of the database for WordPress */
define(‘DB_NAME’, ‘putyourdbnamehere’);
/* MySQL database username /
define(‘DB_USER’, ‘usernamehere’);
/* MySQL database password /
define(‘DB_PASSWORD’, ‘yourpasswordhere’); <=Update your password here
/* MySQL hostname */
define(‘DB_HOST’, ‘localhost’);
There is still valuable information on your website even though it has been infected.
This data should not be lost if something goes wrong during the cleaning process and all your files are deleted or corrupted.
First, backup the / wp-content / folder via your FTP if you want to make a backup of your WordPress site.
You can find all your plug-ins, themes, images, and videos in this folder.
Make a backup of the following files, specific to a particular WordPress installation:
- wp-config.php – This file stores information from your database such as the database name, database username, database password, and so on. You can find this file in the root folder via your FTP.
- .htaccess – Another important file for server access control. You can find this file in the root folder via your FTP.
- favicon.ico – This is the favicon file of your website. You can find this file in the root folder via your FTP.
- robots.txt – This file is used to give instructions on your site to crawlers/web robots. You can find this file in the root folder via your FTP.
All your pages, blog posts, and comments are stored in your WordPress database.
Your blog posts, pages, and comments will be permanently lost if your database is corrupted or deleted.
The following instructions will help you resume your database: Go to the Database section of the hosting control panel, then click the icon of the MySQL or MSSQL database you wish to restore:
Select ‘Backup’ from the Actions Menu
The name and location of the backup file should be noted
It is usually located in / _db_backups.
Using your FTP, navigate to the folder where the database file is located (in our case, / _db_backups) and download it.
Upload the latest updated database file from your folder before uploading it via FTP.
Ensure that your website, database, and other important files are backed up at least once a month before upgrading your WordPress version.
You should make two copies of the backup files/folders and store them on different hard drives in case one is lost/corrupted. At WPHH, we take backups for every malware-infected website.
It is faster to detect malware with Chrome than with any expensive scanner.
For this reason, you should always use the Google Chrome browser when you visit your website and other websites.
Malware can be detected very quickly, sometimes even before Google Webmaster Tools displays a malware warning.
Acting quickly and removing the malicious code/files from your server can sometimes prevent Google from labeling your website as infected or remove Google blacklist warnings.
Visit the Google Safe Browsing Diagnostic page for your site: https://www.google.com/safebrowsing/diagnostic?site=www.mywebsite.com.
Use your domain name instead of mywebsite.com.
The purpose of this page is to provide you with clues about malware issues.
Malware or Malicious code is hosted on the websites delimited by the rectangle above, and hackers have hidden links to these websites somewhere on your website.
In WordPress themes and plugins, hackers usually place these links somewhere. Scan Malware in WordPress Themes and Plugins.
In any case, sign up for Google Webmaster Tools now to learn more about your malware issues.
Go to Health> Malware and see the sample URL containing malware.
Using these sample URLs, you can sometimes search for and delete malicious files on your server quickly.
To detect malware served to Google, use the Find tool (under the Google Search Console Health menu).
Hackers sometimes insert malicious code into WordPress files instead of downloading malicious files.
Specifically, hackers target theme files to insert malicious code that can survive updates and reinstallations of WordPress. [NOTE: scan php files for malicious code]
There is usually malicious code inserted through the IFRAMES and NOSCRIPT tags. [NOTE – scan javascript for malicious code]
Look for these items specifically in your files.
It can be a link to an executable file (such as .exe, .cmd, etc.) or a script that downloads software or redirects users to malicious sites.
- Download a new copy of the latest WordPress and store it on your hard drive.
- To get an idea of the data that is typically included in a typical WordPress installation, browse the files in the different WordPress folders on your hard drive.
- Once you have browsed the folders, access your web server via FTP and look for suspicious files (files that should not be there but are present) in / wp-content /, / wp-admin / and / wp -includes / folders.
In typical WordPress installations, the CSS.php file is usually not present in the / wp-includes / CSS / folder.
If you find one, it’s probably malware.
Backup this file, then delete it from the server so that you can restore it if your website malfunctions.
Searching for malicious files is easy by comparing the name and number of files on your server with those in the new WordPress installation.
Among the most popular places for hackers to store malicious files is the “upload” folder under /wp-content/.
Check this folder regularly.
If you find IFRAME tags in the HTML code of your web pages with width = 0 and height = 0, fix them.
They are usually found at the top or bottom of a webpage’s HTML code as invisible IFRAMES.
A strange code can be found by searching.
Delete blocks of numbers, letters, and unintelligible symbols in your files’ code.
For example.
%wwwww%xxxxxx%yy%%%\u9900\u
Hackers use these encrypted codes to hide malware.
Use the “custom features” of WordPress to search for malicious code.
It is common for malicious code to be injected into user-generated content areas such as comments.
Search your website using the “custom filters” of the “Screaming Frog SEO” spider for spam words (such as viagra, buy, porn, casino, insurance, work from home, etc.).
To search for spam on your website, you can use the site command: search on Google.com.
As an example: site: www.abc.com Real Estate returns all pages on your website that contain the word “Real Estate”.
Check Google’s Webmaster Tools for search query reports as well.
Your website may be infected with malware / spam if it receives many impressions for search terms like “casino”.
Redirects left open to arbitrary destinations are called open redirects.
Malicious websites are often redirected to your website by hackers.
Search for URLs such as www.abc.com/db.php?url=
There was no easy solution to open redirect issues that I found.
Use your web developer or system administrator.
Examine all your internal and external links and check for links to unknown sites.
The malware-hosting website usually has an unintelligible name, such as bacxwq, and ends with .ru.
With Screaming Frog, Google Webmaster, or Open Site Explorer, you can scan your links.
By tracking exits (or outbound links) at the site level, you can easily see where your website is sending traffic.
You should check all the files that can be downloaded from your website. Sometimes hackers add malicious code to these files. You should also delete the following files from your web server.
They are all kind of malicious files that are used to spread malware:
- /wp-includes/js/jquery/jquery.js
- /wp-content/upd.php
- / wp-content / themes / [theme name] /temp/e9815adced6d3.php (or similar)
- wp-includes / xmlrpc.php and wp-includes / css / css.php
- wp-admin / upd.php and wp-includes / css / style.php
- Delete all image files, zip files and other files that are no longer needed. They could have been compromised.
- Delete all plugins that are no longer used and WordPress themes (from the / wp-content / folder) that are no longer used.
To monitor any changes to your robots.txt file, use Robotto ().
There are usually 92 lines of code in this file and it ends with the following code:
require(‘./wp-blog-header.php’);
…Delete this portion…
?>
In other words, delete everything between these two lines.
One of the most popular files used by hackers to add malicious code is this one.
Malware is usually hosted on a website that redirects visitors to your website.
Make sure to check the entire file from top to bottom when looking for malicious code.
There are times when malicious code starts after hundreds of blank lines in your .htaccess file. Also see – how to fix a hacked WordPress .htaccess file
As a result, the code cannot be detected.
The Timthumb PHP script resizes web images in blogs.
Scripts like this are not malicious in themselves, but hackers commonly use them to spread malware.
Timthumb is used by some WordPress plugins and is vulnerable to hackers.
To identify WordPress plug-ins that use timThumb, use the WordPress Vulnerability Scanner plugin.
It is recommended that you either remove or update these plugins.
After your website has been hacked, malicious code called a “backdoor” will be installed.
Backdoors are designed to allow hackers access to your website.
If one backdoor is lost during manual removal or upgrading, several may be installed.
It is still possible that a backdoor has been installed on your website after it has already been hacked.
The only way to find such backdoors is to check each WordPress template file, each plugin, and the database. But this takes time and is not very effective. If you miss something, you have left your backdoor open.
So I suggest you to-
- take your theme files, your database and other important files (such as .htaccess, robots.txt, wp-config.php) and delete all the files, plugins and folders in your directory. WordPress.
- Delete the directory structure of your blog completely, then install the new version of WordPress.
- Do not rely on reinstalling or upgrading your WordPress.
- Although reinstallation/upgrade can replace files with malicious codes with new code, this does not always remove malicious files already placed on your web server.
- Analyze your theme files, your database file and other important files with the anti-virus / anti-malware software installed on your system before downloading them back to your web server.
You cannot recognize users with administrator privileges.
It is possible for hackers to insert malicious code/files on your server if they have administrator rights.
Delete such administrators if you find them. Read more on How to Delete Hidden Admin Users in WordPress?
Scan your computer regularly for malicious files, Trojans, and viruses.
When your computer’s hard drive is infected with malware, your website’s files may be infected/re-infected.
NOTE: A common misconception among webmasters is that malicious robots can be stopped by a robots.txt file. Malicious robots ignore robots.txt files.
After GoDaddy taught me all the tips in the book to get rid of malware, I did just that.
If you ask GoDaddy to remove the malware, you get this pathetic copy-and-paste response:
Please consider removing your website immediately to avoid infecting visitors and act quickly to identify/remove the malware. -Godaddy.
Their emails always end with the following line to further annoy me:
If there is anything else we can do to assist you, please let us know
Sincerely
Godaddy
Online Support Technician
Sometimes the vulnerabilities belong to the web hosting service provider.
Your website may be vulnerable to hacking because of server configuration issues or security vulnerabilities on the hosting platform.
Choose a local host (so you can call him in case of an emergency) and average size. Avoid web hosts that boast of having tens of thousands of customers. Their processing time is extremely slow, and most of them don’t care about you at all. If you operate a WordPress website, choose a web hosting company that specializes in “Secure WordPress hosting for small business sites.” I would recommend Host & Protect, because they provide secure web hosting for small businesses.
Your WordPress problems will be solved by a staff who knows WordPress well. Avoid shared hosting. Shared hosting accounts are far from secure.
To diagnose malware problems on time, Codeguard.com has been found to be the only service that has proven useful so far.
Codegaurd is not a subsidiary of mine, but it has proven useful to me.
When your website’s code changes, it automatically makes a new backup and notifies you via email.
There will be one or more files added to your web server every time you add a new blog post, so you’ll receive email alerts.
When you add/remove plugins, you will receive e-mail alerts because your web server will add/remove files.
You will receive email alerts if a malicious file is secretly added to your web server.
It is important that you pay attention to these emails and do not ignore them.
As a result, I have paid the price.
Changes that look malicious or unknown should be looked for.
Then, if css.php is added to your web server, you should delete it immediately since it is not a standard WordPress file and is most likely malicious.
In spite of all the steps you have taken to remove the malicious code/files from your website, there is no guarantee that it won’t be hacked again.
By exploiting security vulnerabilities in WordPress themes, hosting platforms, or networks, hackers can create new backdoors.
In order to prevent your website from being hacked again, you need to hire someone or hire an intrusion-testing company.
They will intentionally exploit security vulnerabilities in your WordPress theme, your hosting platform, and your network to determine the level of security.
Testers act as hackers to discover security flaws on your website during this type of test.
The results of intrusion tests will pay off and can help you greatly in preventing other malware attacks in the future.
When your website is malware-free, change all your passwords, WordPress security keys, and salts.
Put your website online by deleting the ‘Website Maintenance Page’.
By visiting Health> Malware> Request a Review, you can ask Google Webmaster Tool to review your website.
As long as Google does not detect any malware on your website, it will remove malware warnings within about a day.
If not, malware will remain aware and you will be notified via Google’s Webmaster Tools.
Check the security of WordPress in 30 seconds
It has achieved a market share of about 25% of all existing websites in the world, making it the most popular platform in the world. WordPress has an impressive community and almost endless possibilities. However, it has also become the world’s most attacked platform, and little is done to protect it. You can, however, protect your site from most common attacks by hackers by making a few simple modifications.
- Malicious Code Injection WordPress “Banco De Oro Hack
- Web Shell PHP Exploit
- WordPress Arbitrary File Deletion Vulnerability
- WordPress Pharma Hack
- WordPress hacked redirect
- WordPress Backdoor Hack
- Japanese Keywords SEO Spam WordPress
You can enlighten yourself about most famous WordPress security exploits by reading the blogs provided above and avoid losing hundreds of hours of work!
The method you choose depends a lot on the backup and prevention work you did before. If you know who entered or at least how it entered, you can delete / correct the files in question to “patch” the vulnerability.
You can opt for the brutal solution by reinstalling your server, but be aware that the hacker will return if you reinstall over a fallible site.
- Analyze the server and the site
It is possible to have your server and site scanned using vulnerability scanners. Both free and paid scanners are available online.
An ethical hacker can also perform an intrusion test, offering a variety of services such as a black box security audit (the hacker does not know the inner workings of the system) or a white box security audit (the hacker does know the inner workings of the system). Though these services are usually reserved for large companies, if you know how to hack, you will still be able to detect and foil most attacks on your site or server.
- Install intrusion detection tools
There are two main groups of tools: The first checks machine intrusions, the second checks network intrusions.
Snort is probably the most popular, and you will need to follow safety rules.
Install any updates and observe whether the patches in updates correct the vulnerabilities.
The passwords for your account (and all other accounts on the site and the server), the passwords for the database, and so on, should be changed regardless of the security level of your site. The pirate can return to a site without fear if he has been given a word of the pass.
To put it simply, Perfect Web Solutions will check a set of important points for the security of your site that is unfortunately very often ignored: Also refer to our detailed guide on how to secure your wordpress in 2023.
- Is your version of WordPress visible in your source code?
- Do you limit the number of login attempts to your administration interface?
- Is your wp-config file protected?
- Are your directories accessible to everyone?
- It’s simple and fast! Enjoy!

















